Illegal Eavesdropping
Questions you may be asked by the technician
- How long have you or feel that you have been under electronic surveillance?
- You will be asked to describe briefly what you have been experiencing.
- Do you know the motive and reasons behind the compromise and eavesdropping?
- Have you ever had an experience with a stalker?
- Have you ever filed a restraining order against anyone or had one filed against you?
- You may be asked to list all names of people that you feel may be responsible for this compromise.
- Are there any new or recent guests, maintenance workers?
- Do you think your vehicle is bugged or being tracked?
- What computer(s) do you have at home? i.e., laptop, desktop, Mac, or Windows
- What type of cell phone(s) do you have? Brands and models of cell phone.
- How long have you had the cell phone in your possession?
- Does anyone else have access to your phones.
- Does anyone else besides you have access to passwords to Wi-Fi, computers, Netflix, etc.?
- What is most important to you, a) to stop the eavesdropping surveillance, or b) to catch the perpetrators and suspects that are responsible for the compromise?
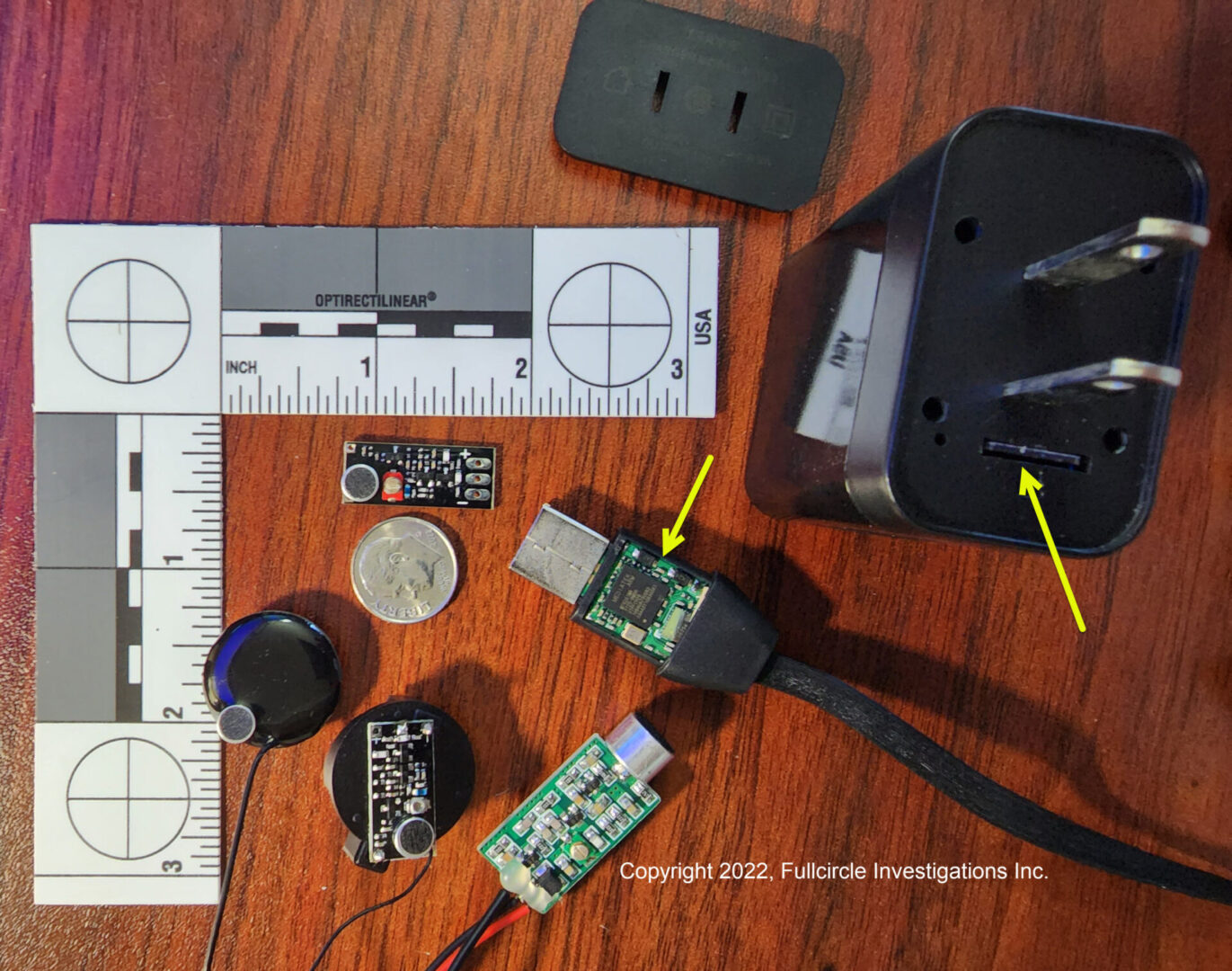


THE SWEEP
During the actual sweep, the technician will ask for you to turn off your cell phone or at the minimum place the phone on airplane mode. our technician will perform a comprehensive visual, physical, and electronic inspection to determine the presence and location of all electronic eavesdropping devices. During this time, we survey AC electrical outlets, telephone cables, and other wiring capable of transmitting communication. We look for wiretaps, Unfriendly hidden cameras, and other intercept devices.
We will also identify other technical weaknesses that may exist in your security posture of the location be it residence, business, boat, plane, or recreational vehicle.
During physical inspections, we examine furniture, outlet covers, ceilings, and other locations common for eavesdropping devices such as microphones, recording devices, transmitters, and camera systems.
After the technician is complete with the TSCM bug-sweep, if an unfriendly hostile device is located, we will provide a detailed written report of the results at no charge.
